Table of contents:
–What is the impact on companies?
– How can companies become NIS2 compliant by 2024?
What Is NIS2?
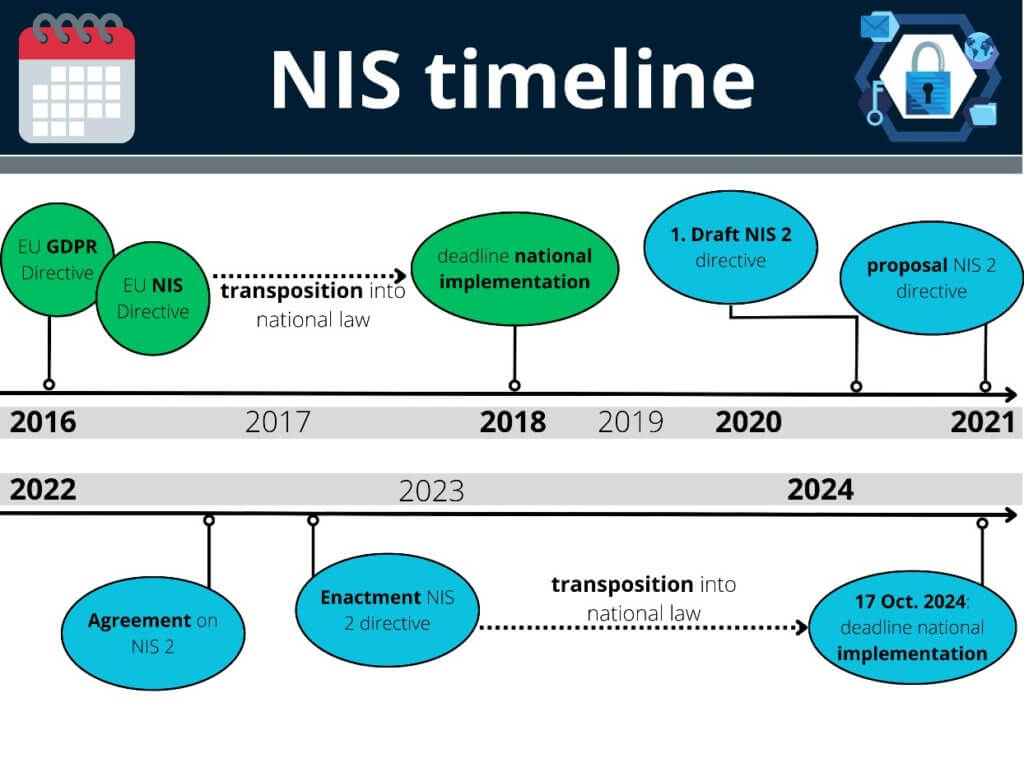
NIS or the Directive of Network Security was first Introduced in the Year 2016. It was designed to protect Critical Infrastructure from all kinds of cyber threats in Europe. The New Directive, the NIS2 is a step-up from the previous directive and expands the scope further to create an all-encompassing cyber security standard.
From past experiences we have seen that cyber criminals often target critical infrastructures and organisations that support the foundations or functioning of essential services for governments and companies. With the new directive the European Union aims to address critical vulnerabilities to create a high level of security and in best case scenarios prevent cyber-attacks, and in the worst case, facilitate recovery and resilience.
The NIS2 directive requires organisations and critical infrastructure to adhere to stricter security and reporting obligations. Compared to the previous directive, NIS2 applies to a wider range of organisations and companies.
Let’s consider the 5 pillars of NIS2:
- introduction of the cyber crisis management structure or CyCLONe
- creating stricter reporting obligations and weaving that into the framework of security structure
- focus on new areas of interest such as supply chain, vulnerability management, cyber hygiene, core internet and more
- introduction of peer reviews for enhancing collaboration and knowledge sharing for all member states
- include more sectors and industries within the scopes of cyber protection to safeguard a larger share of the economy
Why is the NIS2 Important?
The NIS2 broadens the scopes of Cyber Security and Preparedness for Crisis Management. The NIS2 was conceptualised in the wake of the pandemic years when cyber threats became more rampant and alarming. Reports show that in recent times, both the number and the nature of cyber threats and attacks have changed to Impact a wider range of industries and entities. The protective measures should also become more all-encompassing to shield as many critical bodies as possible. Hence the new directive has come up with a more comprehensive policy to strengthen the cybersecurity and resilience of essential service providers in Europe.
Stefanie states,
“NIS2 as a topic is now on the table of CISOs and Board Members as they will be personally taken into account for a sufficient implementation of the directive within their organisations. Facing penalties for not following the regulation is a new level of responsibility“
The changes and the new aspects covered by the NIS2 emphasis on the preparedness factor. This new directive doesn’t differentiate between operators of essential service and digital service provider, instead it focuses on all essential entities and important entities based on their size, impact and sector. As such, the following requirements are the ways in which the NIS2 will help critical infrastructure of essential and important services to stay prepared and combat cyber threats.
– Development and maintenance of a European vulnerability registry: The vulnerability registry will record and maintain newly discovered cyber vulnerabilities throughout Europe. A study for “Coordinated Vulnerability Disclosure (CVD) and Vulnerability databases” was commissioned and concluded in 2021 which will support vulnerability management and the vulnerability database for all member states.
– CyCLONe or the Cyber Crisis Liaison Organisation Network: This is a cooperative network for European member states that are in charge of cyber crisis management. This network along with a cooperation group will facilitate a strong collaboration for information exchange and situational awareness. It will also provide links between the technical level (EU CSIRT Network) and the EU political network.
– Annual report on the state of cybersecurity in the EU: The annual cybersecurity report will help member states stay updated on their annual cyber security performance, areas of improvement and cyber threat situation.
– Documenting all cross border digital service providers: Creating and maintaining a report of all the entities providing cross-border services such as cloud computing, data centre services, DNS services, TLD name registries, domain name registrations and more.
– To enable peer reviews for member states to help all member keep their cyber strategies updated.
– Setting up Computer Security Incident Response Team (CSIRT) and a competent national network and information systems (NIS) authority cooperation among all the Member States.
What is the Impact on Companies?
There’s less than 600 days left for the NIS 2 to be converted into national law. Use the time to raise your awareness on the cybersecurity regulations and start the implantation process.
If you are an essential or important essential entity, then this policy requires you to implement the new policies on risk analysis and information security, business continuity, supply chain security, incident handling, information systems development practices including vulnerability disclosure, cryptography, encryption, and multi-factor authentication. Additionally, you may also be required to adhere to specific ICT (Information and Communication Technology goods) products, services, and processes which have been approved by the Cybersecurity ACT under ENISA. Stefanie recommends seeking expert advice and solutions to assist with NIS2 compliance:
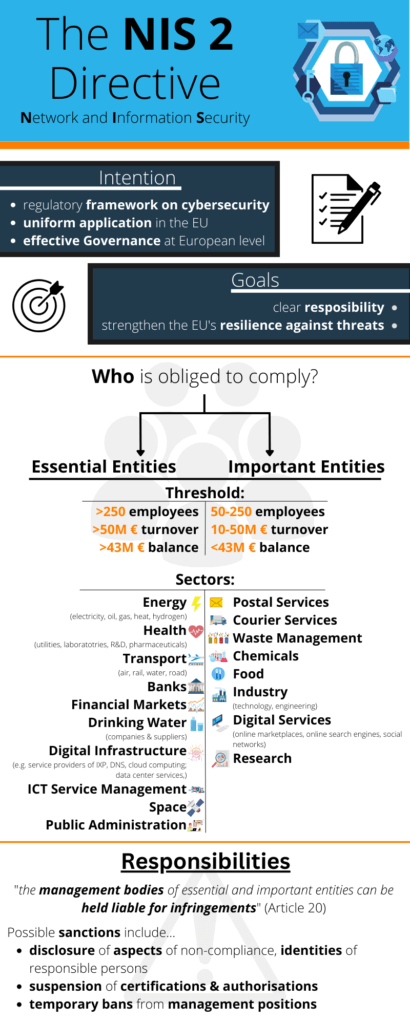
| Essential Entities (EEs) | Important entities (IEs) |
|---|---|
| Large operators from eleven essential sectors and special cases. | Large operators from seven Important Sectors and medium-sized operators. |
| Large Threshold with: more than 250 employees more than 50 M€ turnover more than 43 M€ balance | Medium Threshold with: 50 to 250 employees a turnover between 10 and 50 M€ a balance less than 43 M€ |
| Energy (electricity, oil, gas, heat, hydrogen) | Health (utilities, laboratories, R&D, pharmaceuticals) | Transport (air, rail, water, road) | Banks | Financial markets | Drinking Water Companies and suppliers | Wastewater Companies and suppliers | Digital (provider of: Internet Exchange Points (IXP), DNS service providers, TLD name registries, data centre services, cloud computing service providers, content delivery networks, trust services) | ICT service management |Space | Public administration | Postal services | Courier services | Waste management | Chemicals | Food | Industry (technology and engineering) | Digital services (online marketplaces, online search engines, social networks) | Research |
| EEs will be supervised proactively. | Important entities (IEs) will be under a reactive supervisory regime. |
| For Essential Entities (EE), administrative fines may be up to 10 million euros or up to 2% of the total annual worldwide turnover of the company to which the entity belongs during the previous financial year, which is positively higher. | For important entities (IEs), the NIS2 directive allows for administrative fines of up to 7 million euros or up to 1,4% of the total annual worldwide turnover of the company to which the entity belongs during the previous financial year, which is positively higher. |
| In case of non-compliance penalties are significantly higher for essential entities. | In case of non-compliance important entities will face lesser penalties than essential entities (EEs). |
“If you are not an expert in cyber security it is time to go and look for partners that help to implement the requirements. We are speaking not just about advisory partners, legal partners but also solution partners.”
As you might have guessed already, NIS2 is not just about the preparation phase but equally about the crisis response phase. To that effect, it is crucial that essential entities and companies follow the incident reporting obligations once they encounter a threat or an attack. If the entities can report incidents more precisely and in time, then they are more likely to contribute to the overall learning and growth. The incident reporting process includes issuing an early warning within the first 24 hours of becoming aware of the incident or the possibility of it. The next aspect that follows is the incident notification within 72 hours from being aware of the incident. The notification supports with an initial assessment of the incident’s severity, impact and indicators of compromise. Lastly, a final report is generated within a month after the incident notification which describes the incident in detail along with its root cause analysis.
How can Companies become NIS2 Compliant by 2024?
On-site inspections, security audits, scans, access to the cybersecurity measures that are adopted by the companies/entities and proof that the necessary cybersecurity measures have been implemented by companies/entities are some of the things that companies can expect more of as part of the NIS2.
Stefanie frames the six key-steps that every firm should follow for implementing the NIS2:
1. Assess how the NIS2 impacts you or if you are covered by it
2. Identify partners that can help you to become compliant.
3. Conduct a Gap-Analysis together with experts in the field
4. Create awareness on board level and develop a plan to implement the missing requirements
5. Allocate concrete budgets and if possible, a team to the project
6. Implement missing measures, strategies and routines already now to be compliant by 2024
Companies should already look for ways to implement these changes so that they can become compliant by the 17th of October 2024. NIS2 also comes with heavy penalties for non-compliance of policies (fines of €10 million or 2% of global turnover, whichever is higher for essential entities and €7 million or 1.4% of global turnover, whichever is higher for important entities).


Contributed by F24 Experts
F24 is Europe’s leading Software-as-a-Service (SaaS) provider for resilience. More than 5,500 customers worldwide rely on F24’s digital solutions, which support companies and organisations through all areas of resilience. Solutions cover business messaging and service notification, emergency and mass notification, incident and crisis management, as well as governance, risk and compliance.


